
Network cameras that can check indoor conditions even from far away are becoming widespread. However, there is a risk that network cameras will steal images captured by cyber attacks. In the midst of this, security company Mandiant announced the existence of CVE-2021-28372, a vulnerability that can affect more than 83 million IoT devices, including network cameras, around the world. If this vulnerability is exploited, it is possible for users to steal video from network cameras or to break into devices in their homes.
The vulnerability discovered by Mandiant exists in the Kalay platform serviced by ThroughTek, an Internet of Things developer. According to Thrutech, Kalay equipment is used in more than 83 million units worldwide. This includes network cameras, including baby surveillance and security cameras, and Mandiant warns of the risk of exploiting the vulnerability to steal the screen.
In Mandiant, if you look at the attack estimated by the exploitation of the vulnerability discovered this time, the user can view the video stored in the server by inquiring the camera ID that he owns from the device such as a smartphone to the Kalay server without being attacked first. .
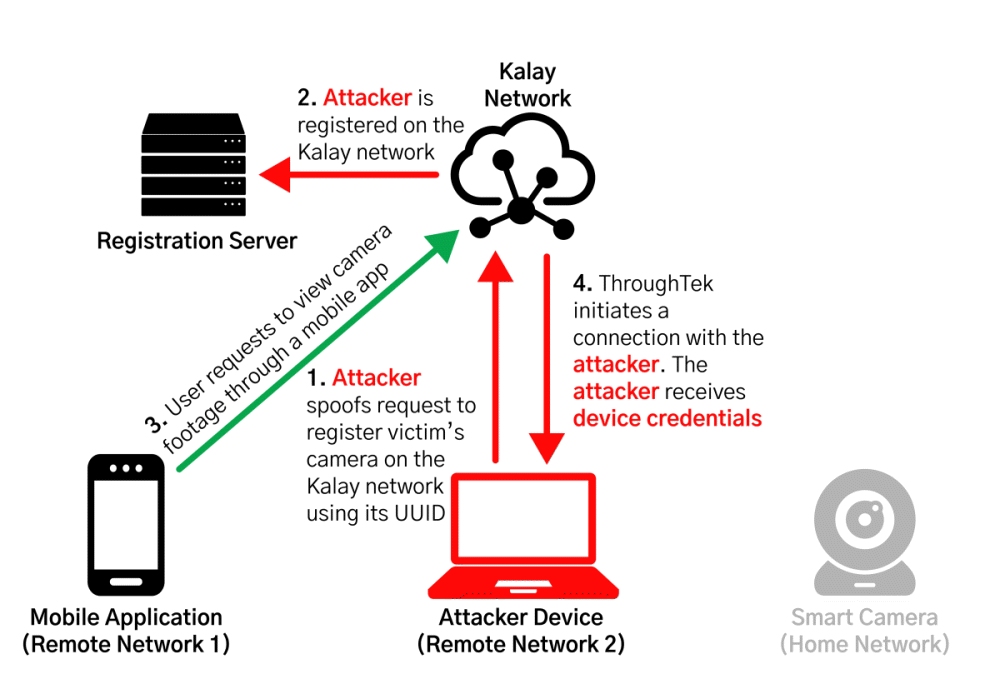
However, if an attacker exploits this vulnerability, it is possible to steal the unique ID of the target network camera. In this state, when the network camera user requests to view the video from the Kalay server, the video data is transmitted to the attacker, not the correct user.
It also points out that another vulnerability in the Kalay network could allow an attacker to gain direct access to the target device over the network. Mandiant reported the vulnerability to CISA, the U.S. Department of Homeland Security’s cybersecurity infrastructure security agency. CISA assigned the vulnerability tracking number CVE-2021-28372 and asked users to minimize network camera online connections.
In addition, Mandiant reports the vulnerability to Thrutech, and Thrutech is developing an SDK that fixes the vulnerability. Mandiant and Thrutech have a message to IoT device manufacturers that have adopted the Kalay SDK to update their SDK to a version with a fixed vulnerability. Related information can be found here.


