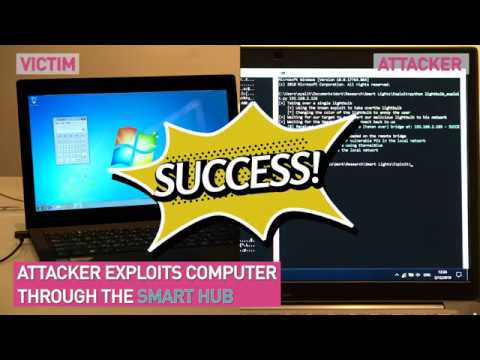
Smart home appliances are on the rise. From smart speakers to surveillance cameras, lighting, and air conditioners, everything is becoming Internet of Things and is connected to the network. Of course, it can be easily controlled with a smartphone. On the other hand, in exchange for this convenience, vulnerabilities are revealed.
Check Point Software demonstrated how IoT devices that communicate with Zigbee using Philips Hue series smart valves are being exploited. Infected Hugh can be manipulated from the outside at will, but the user thinks it is strange and deletes Hugh and adds it again. At that moment, it uses the ZigBee vulnerability to distribute malicious code to the smart valve connection bridge. It then manipulates computers on the same network.
The vulnerability of the Hugh series smart valve demonstrated this time has been pointed out from before. In 2016, drones operated smart valves at once, and in 2017, they warned that there is a risk of spreading malicious codes between smart valves. It proved that it can affect computers or other devices connected to the same network through SmartValve. Once again, the risk of this vulnerability has been highlighted.
Checkpoint Software had already reported the issue to Philips in November of last year. Therefore, Philips released a security patch in mid-January. If you update to firmware version 1935144040, you will not be able to hack this way. However, since there are many people who do not regularly update smart home appliances, there may be concerns about the spread of damage.
In addition, as there are many major brand products such as Amazon’s Alexa, IKEA, and Samsung Electronics as smart home appliances connected by the same ZigBee, you may feel anxious whether similar vulnerabilities exist. Countermeasures may be necessary, such as always using the latest version of the software and establishing another network for smart appliances. Related information can be found here .