TPM (Trusted Platform Module) is a chip embedded in the motherboard to provide security functions and is used in Bitlocker, a data encryption function installed in Windows. However, security firm SCRT reports that it is possible to hack into the hardware directly to steal the TPM key and access bitlocker-protected device data.
The TPM is a chip built directly into the motherboard or added to the CPU, and is responsible for ensuring that the device operating system and firmware have not been tampered with, and safely storing the encryption key. BitLocker, a Windows data encryption feature, typically stores the volume master key inside the TPM, but the SCRT security team has experimented with hacking the TPM to access protected data.
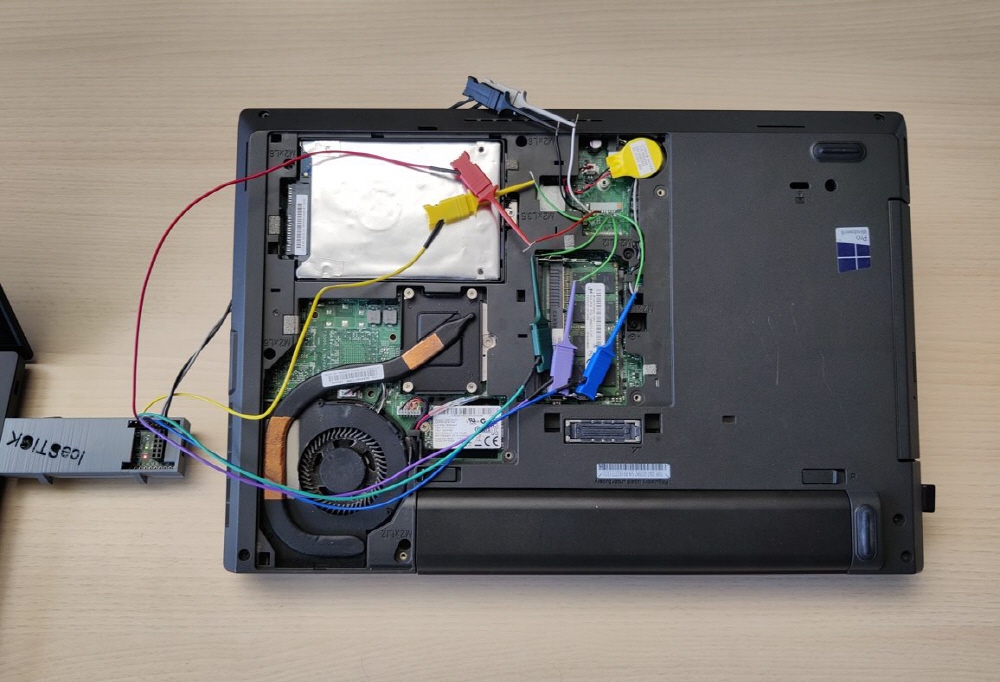
The research team used the Lenovo ThinkPad L440 for the experiment. When the device boots, the TPM checks various system properties to make sure the boot sequence hasn’t changed, and if successful, it releases the volume master key, sends it to the CPU, decrypts the disk, and starts loading the operating system.
In the process of sending this volume master key to the CPU, the TPU is sending a signal using a bus that connects a low-bandwidth device to the CPU, such as an LSP (Low Pin Count) bus. The researchers argue that the slowness of these bus transfers makes it possible to hack into the hardware to detect the volume master key signal and maliciously combine device local operations.
The research team first removed the ThinkPad L440 cover by manually finding the TPM chip to expose the motherboard. Then I found a chip labeled P24JPVSP under the trackpad and thought it was a TPM chip called ST33TPM12LPC using the LCP bus.
Among them, LAD0, LAD1, LAD2, LAD3, LFRAME, and LCLK signals are required to acquire the volume master key, but since the pin spacing is only 0.65mm, it is quite difficult to directly solder the probe that measures the signal. There was also the problem of missing LCLK signals, he said.
Fortunately, the team was able to find the LCP debug pads covered with black tape, which made measuring the signal simpler than soldering them directly to the TPM chip. However, again, the LCLK signal was not connected to the debug pad, so the research team said that they paid a fee to a website that sells motherboard schematics online to obtain the ThinkPad L440 schematic. As a result, it is said that he found out that there was a debug pad with nothing connected, and it was possible to send the LCLK signal to the debug pad by soldering.
The research team soldered the LCLK signal to the debug pad and soldered the probe to the appropriate debug pad. Then, the device was started by connecting with a sniffer, a device that steals LPC signals, and the volume master key signal transmitted from the TPM to the CPU through the LCP bus was received using the LPC sniffer published on GitHub. The volume master key values detected by multiple measurements had deviations that appeared to be due to a less-than-perfect sniffer connection, but they were able to estimate the correct value relatively easily by repeating the measurements.
The research team says that you can actually use the obtained volume master key to circumvent bitlocker protection and to compound local disks. The result is said to be capable of manipulation, such as accessing stored files, throttling them, stealing local password databases, or creating backdoors on machines with malware.
The attack could be executed in days without destroying the device, using tools available in DIY stores. The research team argues that TPM sniffing is technically prevented in TPM 2.0, which is required by the latest Windows 11, but the risk of exposure to other physical attacks remains. Related information can be found here.


















Add comment