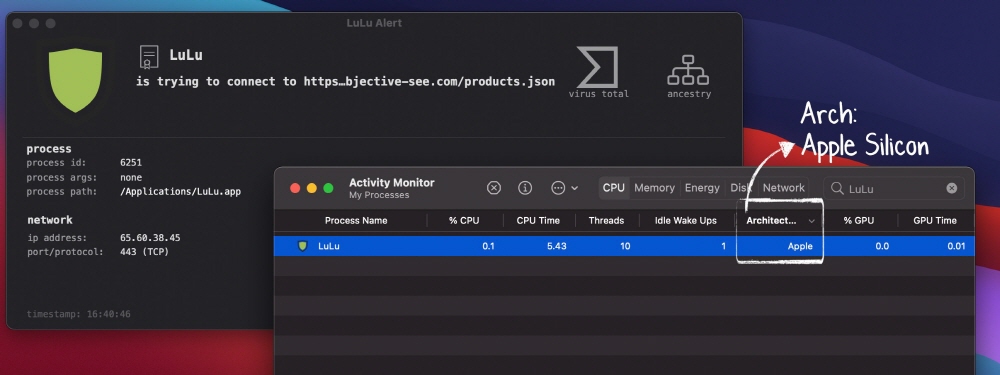
It’s been a while since Apple’s self-developed Apple silicon M1 chip-based Mac was released, but it is said that malicious code that works by default has already been discovered.
The discovery was made by former NSA security researcher Patrick Wardle. According to this, on the M1 Mac, the binary for the Intel chip can run on the Rosetta 2, but what he found was that it contained ARM64 code compiled for the M1.
Specifically, it is GoSearch22.app, an M1 native counterpart to the adware Pirit targeting Intel Macs. It is speculated that this version is aimed at displaying bulk advertisements and collecting data from users’ browsers.
It was VirusTotal, an antivirus site owned by Alphabet, that he discovered such malware. He also pointed out that GoSearch22 was actually signed with an Apple developer ID on November 23, 2020. Apple has revoked the certificate at this point, but mentions that what was found may have infected macOS users.
Moreover, Wardle reported that only 15% of antiviruses that could find the x86 version in VirusTotal could not judge the M1 version GoSearch22 as malicious. In other words, most antivirus software is not ready to respond to malware designed for M1.
In response to the report, another security researcher Thomas Reed said compiling for the M1 could be as simple as putting a switch in the project settings.
At one time, it is common to say that Macs have a lower risk of malware than Windows, but there was also a research finding that Macs in 2019 exceeded Windows. Usually, as the spread of the platform progresses, the targets of attack increase, and as the M1 Mac shows smooth sales, there is a possibility that Apple will be more troubled with security measures in the future. Related information can be found here .
Meanwhile, Apple has updated Apple Platform Security, a guide that explains security specifications from its hardware to services.
The February 2021 version of Apple Platform Security covers new hardware security features for Macs based on the Apple Silicon M1 processor, as well as the latest operating systems such as iOS 14, iPadOS 14, and macOS Big Sur. You can search by item on the web and use a PDF format that you can read all at once. 200 pages in PDF version. In the April 2020 version, the number of pages is increasing by 40, including several items being added.
On its own page, the protection of personal information is a fundamental human right, and Apple’s emphasis on personal information and underlying security has been more appealing than before. There are differences in business structure from competitors, but above all, Apple is making strong security with hardware infrastructure including T2 chip and security that can tightly integrate software and hardware developed by the company from bottom to top. .
Apple Platform Security provides a comprehensive description of specific encryption and data protection methods for these security efforts. Guides are not only helpful to developers, but also related to safety, including general users. Most of the additions in the February 2021 version were Mac security specifications that adopted Apple Silicon. Apple has secured hardware-based security by mounting its own processor T2 in the existing Mac, but the M1 includes the main processor. In addition, Apple has integrated security-only components into the chip a few years before its launch, which significantly improves hardware security compared to previous Macs.
Guides can be searched by item on the support page, and can be viewed in PDF format at the bottom of the page. In addition, you can refer to the Johns Hopkins University researcher’s report for data security including iOS restrictions compared to other mobile devices. Related information can be found here .

















Add comment