According to cyber security firm Darktrace, the number of cryptojack attempts to unauthorizedly extract passwords from someone else’s hardware has increased by as much as 78 percent in 2018.
Attacks targeting such monetary benefits tend to be prudent. A recent example of a cryptojack is a good example. Of course, this trend continues this year. A Ransomware attack could be a better way for an attacker as the victim could not make a coin settlement bit coin in technical mistakes.
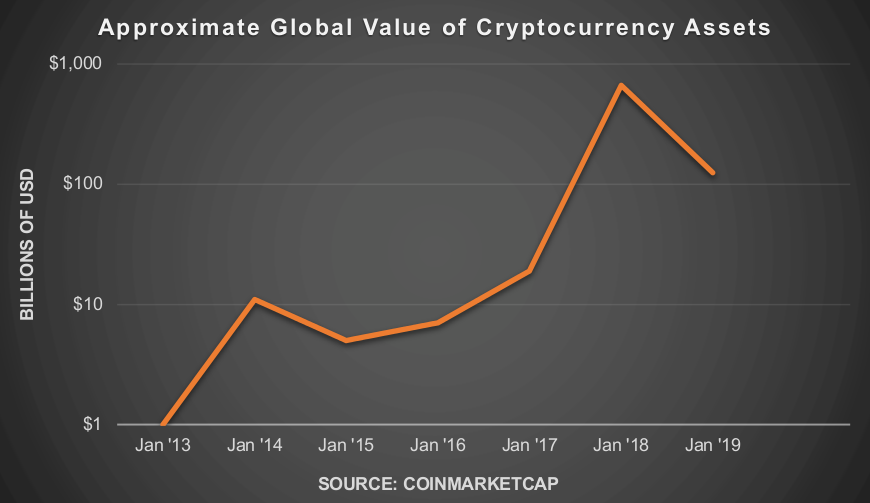
Of course, unlike Ransomware, Cryptojack is a kind of action that slowly penetrates and guarantees profit. For an attacker, it is also advantageous that the entry barriers are low. Other methods, such as credit card information theft, are quite cumbersome for criminals, for example, to build a money laundering structure to avoid tracking government agencies.
This attack is mainly for cryptographic monetization, which is different from bitcoin, and Monroe is suitable for operating on common hardware that consumers own. For more information, please click here .

















Add comment