
Microsoft has been hostile to Linux, as Steve Ballmer, who served as Microsoft’s CEO at the time, said in 2001 that Linux was the enemy. However, after Satya Nadella took office as CEO in 2014, Microsoft changed its policy significantly and joined the Linux Foundation in 2016 or is showing a concession attitude, such as installing WSL, a structure that runs binary files for Linux on Windows. . In the midst of this, an engineer working for Microsoft reveals the in-house Linux distribution and summarizes its usage and features, attracting attention.
According to this, the internal distribution was created by the team that made the Linux kernel used in WSL2 under the name of CBL-Mariner, and was distributed for use in cloud infrastructure and edge computing.
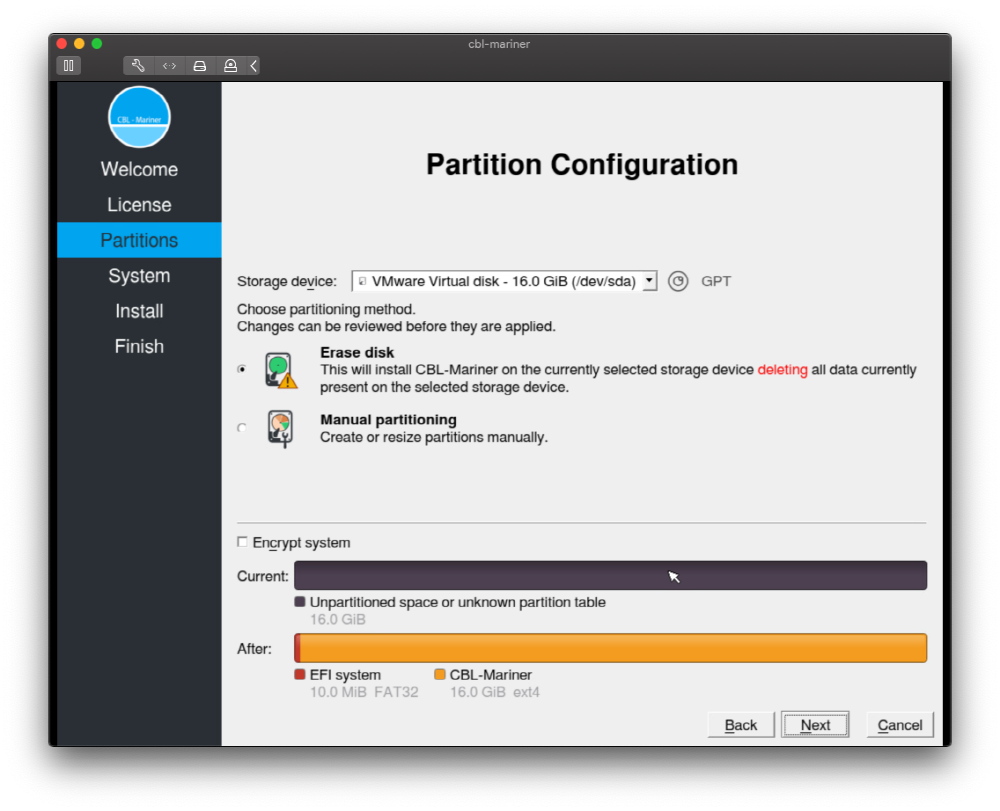
CBL-Mariner is open source and can be downloaded by anyone from the Microsoft repository. But now, it is not distributing the build image that is easy for the general public to use, but to use it, you have to read the document and build it yourself. As a demo, he even ran a build by entering code that meets the build requirements to generate an image file to be installed in the server virtualization tool (vSphere). Then, he said that the VM settings are ‘Other 5.x or later Linux (64-bit)’ for the guest OS and 1 vCPU, 2 GB of RAM, 16 GB of Di or 16 GB of RAM. You can choose between text mode and graphic mode for installation mode, and here you choose graphic mode. In addition, two installation types can be selected: Core and Full. According to him, the core installation can be done in 29 seconds and the pool can be installed in about 76 seconds. It also performs partition or system setup during installation.
CBL-Mariner is written with reference to Fedora and Photon-OS, and is said to be quite similar to both distributions. Also, since the SSH daemon was not installed in the initial state, he installed the SSSH daemon from the vSphere console.
The CBL-Mariner package system is RPM-based, and both dnf and tdnf are used for update, and an image-based update system using the RPM-OS tree is also supported. After installation, available software is organized in two package repositories (base and update), and 3,300 packages are prepared.
In addition, CBL-Mariner is focused on security, and the design is made based on the security principle (Secure by Default). In addition to kernel and compiler-based countermeasures, updates are signed, address space placement, and random and log tampering countermeasures are also implemented. The security elements adopted for CBL-Mariner can be found in the GitHub repository. Related information can be found here.


















Add comment